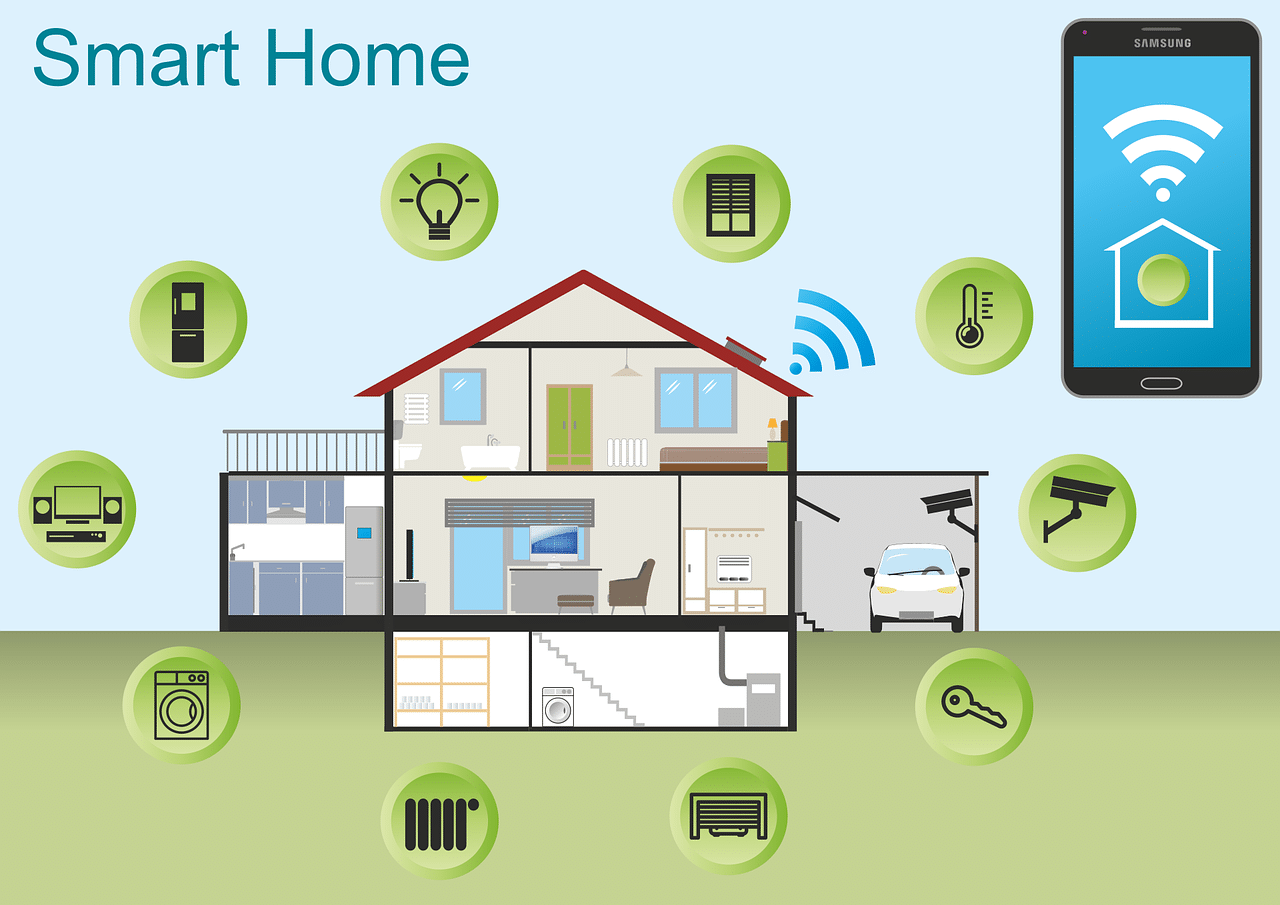
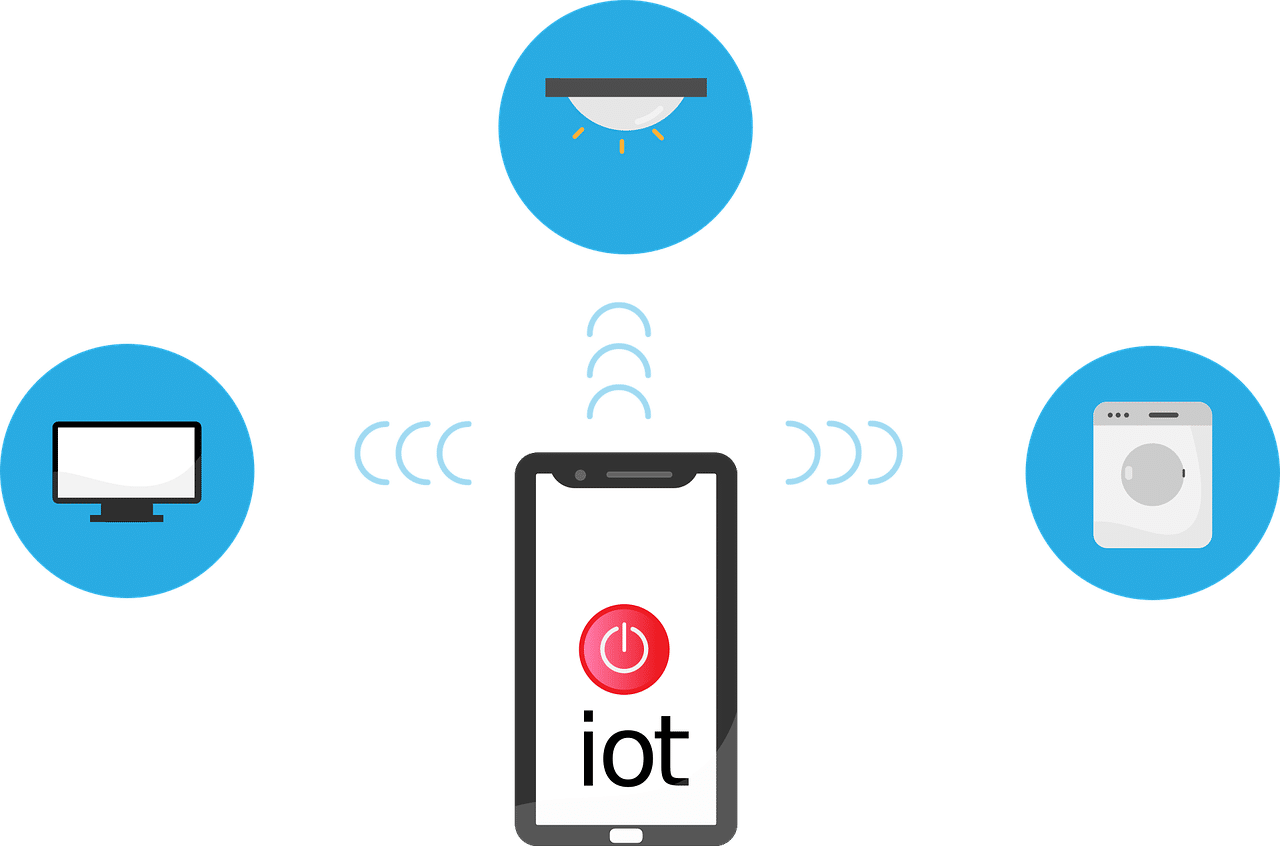
Lost in The Cybersecurity Jungle: Don’t Go Unprepared!
Cybersecurity is like a jungle A sprawling, bewildering landscape that businesses find themselves having to explore. As an IT Provider, we understand the uncertainty that comes with trying to navigate the complexity of cybersecurity. The jungle is vast, threats are hidden in the undergrowth if you...